I have two domain is for sale
1, hevps.com
2, hkvps.cc
If you need to buy, you can send e-mail to me, admin # leisudeng.com. (The # into @)
Tell me the highest price you can give, I will contact you as soon as possible after receipt of the message.
These domain names free transfer and transferred to your domain registrar account.
Camels in the street begging
This year both been led camel begging situation in China, Guangzhou, Shenzhen, Wenzhou, Xiamen and other places. Camels or amputation wound apparently caused by man, these camels are all skinny, health, worrying.
Some netizens questioned broken leg camel apparently unable to walk, so great is how to be shipped to the streets?
How To Protect SSH with fail2ban on Ubuntu 12.04
About Fail2Ban
Servers do not exist in isolation, and those virtual private servers with only the most basic SSH configuration can be vulnerable to brute force attacks. fail2ban provides a way to automatically protect virtual servers from malicious behavior. The program works by scanning through log files and reacting to offending actions such as repeated failed login attempts.
Step One—Install Fail2Ban
Use apt-get to install Fail2Ban
sudo apt-get install fail2ban
Step Two—Copy the Configuration File
The default fail2ban configuration file is location at /etc/fail2ban/jail.conf. The configuration work should not be done in that file, however, and we should instead make a local copy of it.
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
After the file is copied, you can make all of your changes within the new jail.local file. Many of possible services that may need protection are in the file already. Each is located in its own section, configured and turned off.
Step Three—Configure the Defaults in Jail.Local
Open up the the new fail2ban configuration file:
sudo nano /etc/fail2ban/jail.local
The first section of defaults covers the basic rules that fail2ban will follow. If you want to set up more nuanced protection on your virtual server, you can customize the details in each section.
You can see the default section below.
[DEFAULT]# "ignoreip" can be an IP address, a CIDR mask or a DNS hostignoreip = 127.0.0.1/8bantime = 600maxretry = 3# "backend" specifies the backend used to get files modification. Available# options are "gamin", "polling" and "auto".# yoh: For some reason Debian shipped python-gamin didn't work as expected# This issue left ToDo, so polling is default backend for nowbackend = auto## Destination email address used solely for the interpolations in# jail.{conf,local} configuration files.destemail = root@localhost
Write your personal IP address into the ignoreip line. You can separate each address with a space. IgnoreIP allows you white list certain IP addresses and make sure that they are not locked out. Including your address will guarantee that you do not accidentally ban yourself from your own server.
The next step is to decide on a bantime, the number of seconds that a host would be blocked from the VPS if they are found to be in violation of any of the rules. This is especially useful in the case of bots, that once banned, will simply move on to the next target. The default is set for 10 minutes—you may raise this to an hour (or higher) if you like.
Maxretry is the amount of incorrect login attempts that a host may have before they get banned for the length of the ban time.
You can leave the backend as auto.
Destemail is the email that alerts get sent to. If you have a mail server set up on your droplet, Fail2Ban can email you when it bans an IP address.
Additional Details—Actions
The Actions section is located below the defaults. The beginning looks like this:
## ACTIONS## Default banning action (e.g. iptables, iptables-new,# iptables-multiport, shorewall, etc) It is used to define# action_* variables. Can be overridden globally or per# section within jail.local filebanaction = iptables-multiport# email action. Since 0.8.1 upstream fail2ban uses sendmail# MTA for the mailing. Change mta configuration parameter to mail# if you want to revert to conventional 'mail'.mta = sendmail# Default protocolprotocol = tcp[...]
Banaction describes the steps that fail2ban will take to ban a matching IP address. This is a shorter version of the file extension where the config if is located. The default ban action, “iptables-multiport”, can be found at /etc/fail2ban/action.d/iptables-multiport.conf
MTA refers to email program that fail2ban will use to send emails to call attention to a malicious IP.
You can change the protocol from TCP to UDP in this line as well, depending on which one you want fail2ban to monitor.
Step Four (Optional)—Configure the ssh-iptables Section in Jail.Local
The SSH details section is just a little further down in the config, and it is already set up and turned on. Although you should not be required to make to make any changes within this section, you can find the details about each line below.
[ssh]enabled = trueport = sshfilter = sshdlogpath = /var/log/auth.logmaxretry = 6
Enabled simply refers to the fact that SSH protection is on. You can turn it off with the word “false”.
The port designates the port that fail2ban monitors. If you have set up your virtual private server on a non-standard port, change the port to match the one you are using:
eg. port=30000
The filter, set by default to sshd, refers to the config file containing the rules that fail2ban uses to find matches. sshd refers to the /etc/fail2ban/filter.d/sshd.conf.
log path refers to the log location that fail2ban will track.
The max retry line within the SSH section has the same definition as the default option. However, if you have enabled multiple services and want to have specific values for each one, you can set the new max retry amount for SSH here.
Step Five—Restart Fail2Ban
After making any changes to the fail2ban config, always be sure to restart Fail2Ban:
sudo service fail2ban restart
You can see the rules that fail2ban puts in effect within the IP table:
sudo iptables -L
Reprint Please Indicate:How To Protect SSH with fail2ban on Ubuntu 12.04
How To Install iRedMail On Ubuntu 12.04 x64_Tutorials | LEISUDENG
If you would like to create your own online e-mail system, you can use iRedMail. In this article, we will explain how you can do it.
Step 1 – Droplet Creation
We use a 2 CPU Core / 2GB RAM droplet with Ubuntu 12.04 x64 image.
iRedMail is currently supported on Ubuntu 12.04 LTS and Ubuntu 13.04, among many other distributions of Linux.
If you have a domain name you want to use, name your droplet as that domain name, which will become its hostname and reverse DNS record.
Step 2 – Create a Domain Name
For our Cloud Mail purposes, we will register a free domain, cloudmail.tk from dot.tk
Once you have your domain name registered, point it to DigitalOcean’s name servers:
ns1.digitalocean.com (198.199.120.125)
ns2.digitalocean.com (141.0.170.89)
ns3.digitalocean.com (198.199.95.114)
Make sure to check those IP addresses manually, as they may have changed since the time this article was written.
Now open your Control Panel on DigitalOcean and click DNS, located under Labs section.
Click Add Domain and create a new record by pointing your new domain to your droplet’s IP address:
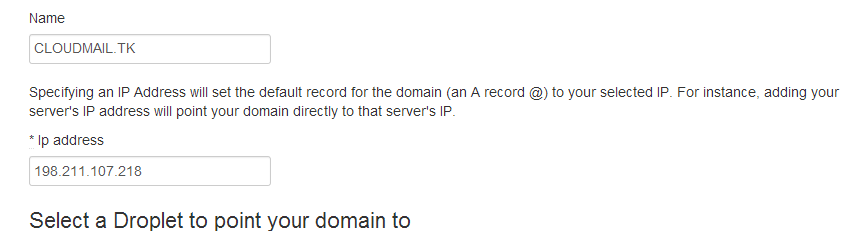
Create a new MX record, make sure to have a trailing dot at the end of your domain name:
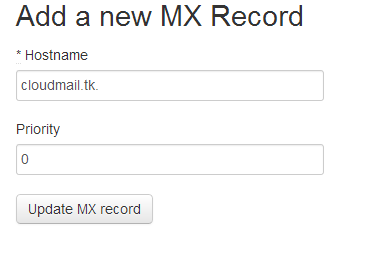
Add SPF records to make sure others cant spoof emails by pretending to send them from your domain.
Make sure to have “-all” in your SPF record, and point it to your droplet’s IP.
The record’s format would be “v=spf1 ip4:IP_ADDRESS -all”
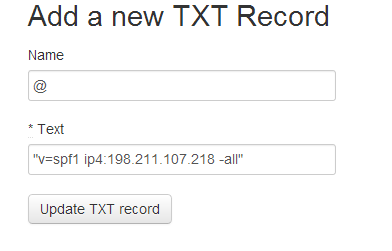
There will be one more record to add after you have finished installing iRedMail – DKIM key.
Step 3 – iRedMail Installation
Make sure to set the hostname of your domain name, if you haven’t done this during droplet creation:
wget https://bitbucket.org/zhb/iredmail/downloads/iRedMail-0.8.6.tar.bz2tar jxvf iRedMail-0.8.6.tar.bz2 && cd iRedMail-0.8.6hostname cloudmail.tkbash iRedMail.sh
You are greeted with a Graphical User Interface Installer by iRedMail:
If you have several droplets, you can even use GlusterFS for distributed, replicated e-mail storage, providing further redundancy:
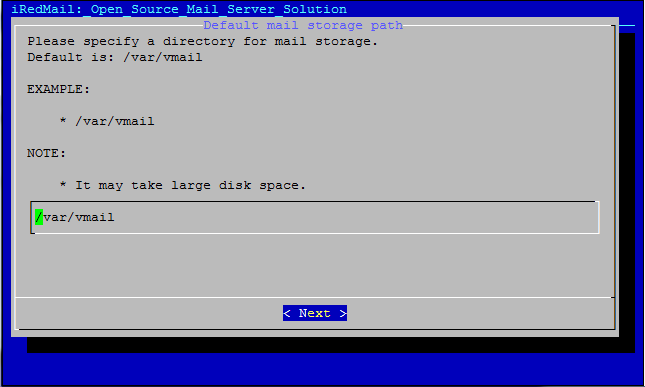
For backend, we chose MySQL. You can also use OpenLDAP and PostgreSQL:
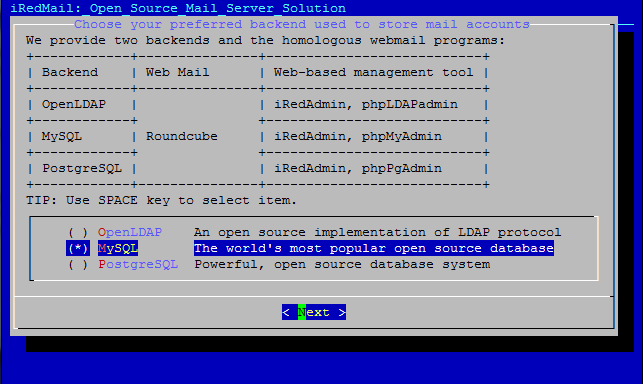
Since we have registered a domain in Step 2, we will place it here:
From package selection, you can omit phpMyAdmin and Fail2Ban.
When asked whether you would like to use firewall rules provided with iRedMail, select ‘No’.
Firewall rules should be custom made for each server, and adopting a DROP ruleset from iRedMail’s package is not recommended.
We would also not recommend using Fail2Ban from their package, as it banned our own IP when we refreshed a page.
Reboot your droplet after completion.
All of the installation notes and logs can be found in iRedMail.tips file ( /root/iRedMail-0.8.6/iRedMail.tips ).
Here you will have information on passwords, SSL certificate locations, and DKIM records.
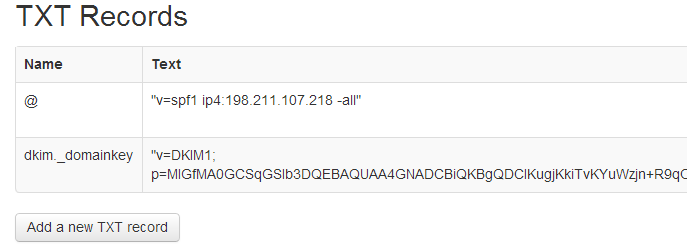
Add the DKIM record to DigitalOcean’s DNS control panel for your domain:
Step 4 – Add SSL Certificate
Although this step is optional if you just want to use self-generated certificate, we would still recommend getting a trusted SSL certificate.
By default, iRedMail will create a self-signed certificate and store it in /etc/ssl/certs/iRedMail_CA.pem and /etc/ssl/private/iRedMail.key
We can get a free SSL certificate from InstantSSL
You would need to create a CSR and private KEY first:
cd /etc/sslopenssl req -out cloudmail.tk.csr -new -newkey rsa:2048 -nodes -keyout cloudmail.tk.key
This will generate 2 files: cloudmail.tk.csr (your Certificate Signing Request file), and cloudmail.tl.key (your private SSL key which should not be shared with anyone).
You would provide the CSR file (cloudmail.tk.csr) to InstantSSL during SSL request.
After they have validated your request, you will receive the certificate file (in zip format) that contains two files:
cloudmail_tk.ca-bundle (your SSL certificate bundle)
cloudmail_tk.crt (your SSL certificate)
Place both files to /etc/ssl and modify /etc/apache2/sites-available/default-ssl
SSLCertificateFile /etc/ssl/cloudmail.tk.crtSSLCertificateKeyFile /etc/ssl/cloudmail.tk.keySSLCACertificateFile /etc/ssl/cloudmail.tk.ca-bundle.crt
Restart Apache
service apache2 restart
Now you should have SSL enabled, and you can proceed to logging in to iRedAdmin (https://cloudmail.tk/iredadmin/ ) with username postmaster@cloudmail.tk and password you provided during installation in Step 3.
From iRedAdmin, you can add new users, new admins, and new domains into your system:
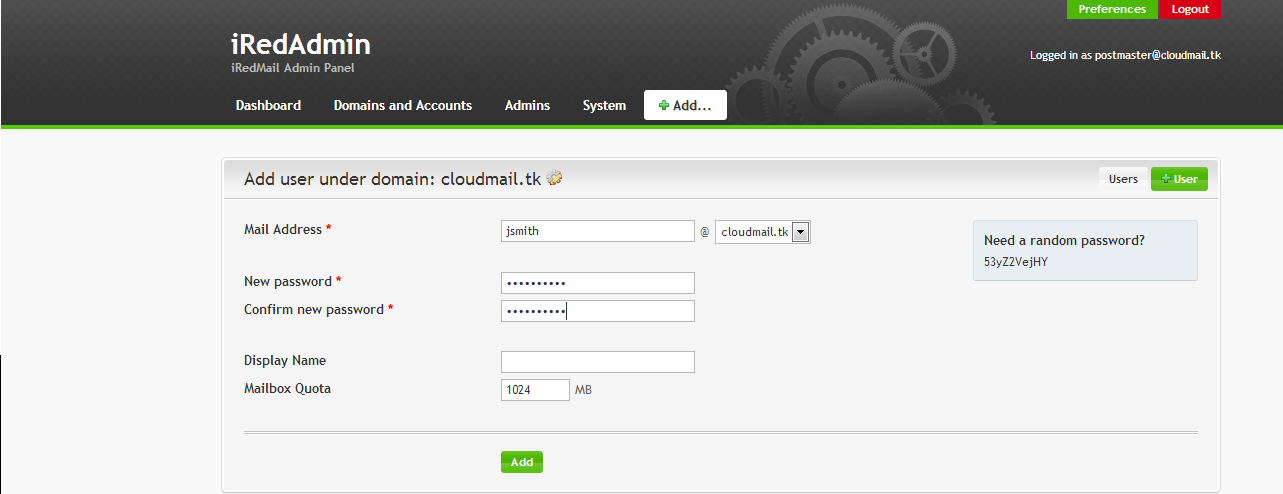
Once you have created an e-mail account, you can access it at https://cloudmail.tk/mail/
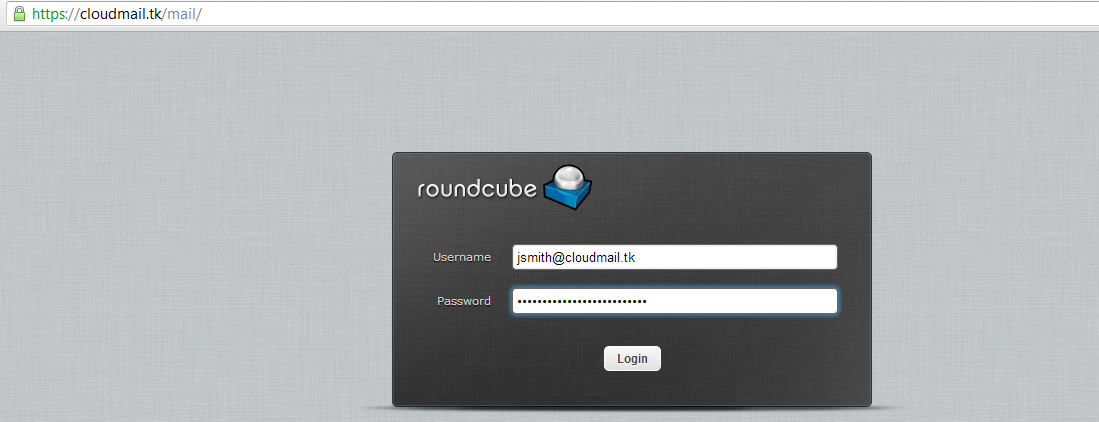
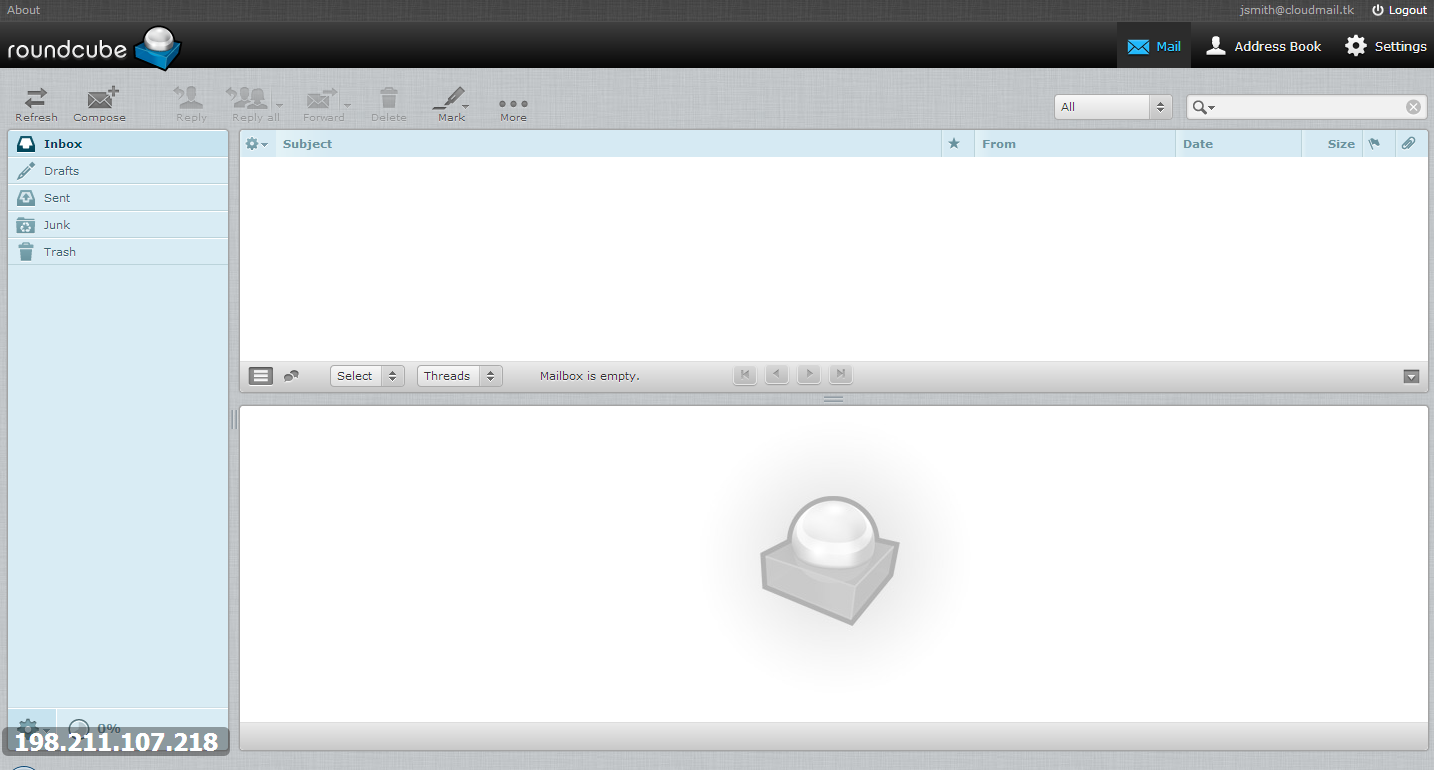
And you are all done!
Reprint Please Indicate:How To Install iRedMail On Ubuntu 12.04 x64
How To Copy Files With Rsync Over SSH
Step 1 – Setup public SSH keys
On our origin server, we will generate public SSH keys with no password:
ssh-keygen -f ~/.ssh/id_rsa -q -P ""cat ~/.ssh/id_rsa.pub
This is our public SSH key that can be placed on other hosts to give us access:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDLVDBIpdpfePg/a6h8au1HTKPPrg8wuTrjdh0QFVPpTI4KHctf6/FGg1NOgM++hrDlbrDVStKn/b3Mu65//tuvY5SG9sR4vrINCSQF++a+YRTGU6Sn4ltKpyj3usHERvBndtFXoDxsYKRCtPfgm1BGTBpoSl2A7lrwnmVSg+u11FOa1xSZ393aaBFDSeX8GlJf1SojWYIAbE25Xe3z5L232vZ5acC2PJkvKctzvUttJCP91gbNe5FSwDolE44diYbNYqEtvq2Jt8x45YzgFSVKf6ffnPwnUDwhtvc2f317TKx9l2Eq4aWqXTOMiPFA5ZRM/CF0IJCqeXG6s+qVfRjB root@cloudads
Copy this key to your clipboard and login to your destination server.
Place this SSH key into your ~/.ssh/authorized_keys file:
If your SSH folder does not exist, create it manually:
mkdir ~/.sshchmod 0700 ~/.sshtouch ~/.ssh/authorized_keyschmod 0644 ~/.ssh/authorized_keys
Step 3 – Rsync files over
Rsync is a great utility, as it allows you, among many other things, to copy files recursively with compression, and over an encrypted channel.
We will copy a file from our origin server (198.211.117.101) in /root/bigfile.txt over to our destination server (IP: 198.211.117.129) and save it in /root/bigfile.txt as well.
Login on 198.211.117.101 and rsync the file over to 198.211.117.129:
rsync -avz -e "ssh -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null" --progress /root/bigfile.txt 198.211.117.129:/root/
If you are using a different user, for example “username” then you would have to append it in front of destination server. Make sure to have your public key in that user’s ~/.ssh/authorized_keys file:
rsync -avz -e "ssh -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null" --progress /root/bigfile.txt username@198.211.117.129:/
The SSH options are useful to keep Rsync quiet and not prompting everytime you connect to a new server.
Verify that you have received the file on destination server (198.211.117.129):
ls -la /root/bigfile.txt
And you are all done!
Reprint Please Indicate:How To Copy Files With Rsync Over SSH
Consult chapter doctor: Create dead engine problem about Lvs!_LVS Tutorials | LEISUDENG
Consult chapter doctor: Create dead engine problem about Lvs!_LVS Tutorials | LEISUDENG.
The Lvs that I introduce our company simply first distributings circumstance. The load that our Lvs becomes Web is balanced. Use 6 PC server in all, among them 2 are done respectively advocate complementary equalizer. 4 true servers!
The system of the server is AS4, the kernel is 2.6 kernels, did not hold any patch orders, install successful Ipvsadm service. Our company used Ipvsadm to do transmit, the other checkup to true server and heartbeat are the program implementation that passes his. Do not have a problem through the test, but, latter of our Lvs advocate alloter happening dies often machine, the configuration of our server is the Cpu that double nucleus gallops, the memory of 2G, advocate the load of the server is in all the time monitoring, with Uptime time statistic, always maintain in 1 ~ 5 between. Discharge is not very big, maintain the flow in 2 ~ 5M, but advocate equalizer lies between on 1 ~ 2 days, ipvsadm service dies with respect to meeting Mo Ming, still create machine dead opportunity occasionally, more strange is the machine died any port do not join on, the bag of Icmp can arrive at a server, restart machine, discovery does not have any having to pass the information at signing up for a fault inside the log! Feel very strange all the time so, is suspicion the program causes a certain place to spill over? Do not know what to method can detect? Consult me this problem is Ipvsadm software spills over problem, still I want how to detect where does Lvs cause to spill over, ? Thank
? Consult Zhang Bo and each elder: Ipvs version problem Consult everybody about two LVS attemper problem?
![46bea3d130171e1de2839d659c6188ca-300x148[1]](https://hkvhost.files.wordpress.com/2014/11/46bea3d130171e1de2839d659c6188ca-300x1481.jpg?w=625)


